The most interoperable and integrated Key Manager in the Market
- Single pane of glass of all cryptographic keys
- Unprecedented Capacity
- Multi-Cloud capability
- Compliance with all FIPS Levels
- Integration Versatility
Delivery Time:
Key Benefits
Details
Utimaco's Enterprise Secure Key Manager (ESKM) offers organizations of all sizes a superior solution for key storage and management capabilities, delivering high security and compliance. It enables unified enterprise key management with reliable policy controls, centralized administration, and comprehensive audit trails. This streamlines operations, reduces costs, and assists in control attestation.
Secure and Manage your Keys for Data at Rest and Data in Use – Fully FIPS-certified
Every organization has customer and employee data that must be protected. By securing the cryptographic keys used to encrypt the data, ESKM guards against attacks, misuse, and data breach exposure which can result in the loss of sensitive data, as well as harming a company’s reputation and brand.
In addition, ESKM provides centralized key management through a single pane of glass, saving time and money for organizations of all sizes.
ESKM is the first industry-certified Key Management Interoperability Protocol (KMIP) v2.1 offering with market leading support for partner applications and pre-qualified solutions, integrating out-of-the-box with varied deployments, as well as custom integrations.
Cloud Integrations and BYOK
ESKM integrates with all major Cloud Service Providers to help organizations transition to the cloud securely. With the BYOK (Bring Your Own Key) concept, enterprises encrypt their own data while retain control of their encryption keys.
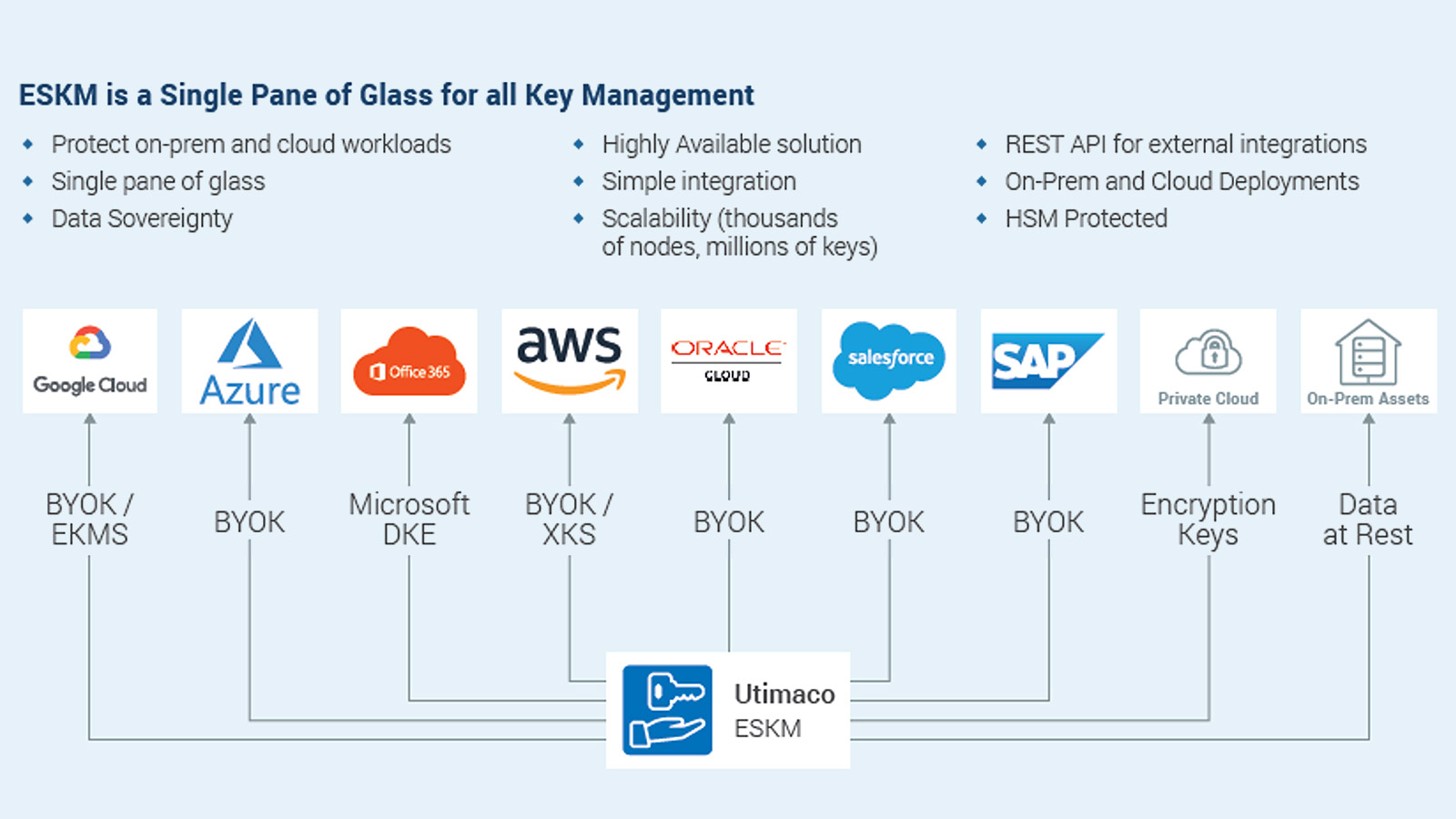
Easy Deployment and Integration
ESKM provides easy deployment and licensing processes. It can be effortlessly installed and configured; simply drop in as hardware or virtual appliance. Access transparent client licensing, with no hidden costs attached to key volume or scalability.
Supporting OASIS KMIP, RESTful API, KMS it enables broad integration versatility. It also comes with included, pre-installed, digitally signed, and verified software for immediate startup and a Software Development Kit (SDK).
Certifications and Compliance
- Compliance:
- FIPS 140-2 Level 1 (ESKM L1 (Virtual appliance)
- FIPS 140-2 Level 2 (ESKM L2 (1U appliance))
- FIPS 140-2 Level 3 (ESKM L3 (1U appliance))
- FIPS 140-2 Level 4 (ESKM L4 (1U appliance))
- Safety: UL/CUL, CE, TUV, BIS, BSMI, SII
- Emissions: FCC Class B, VCCI, BSMI, C-Tick, IC, KCC
- Environmental: RoHS, REACH
Supported Cryptographic Algorithms
- Such as AES, 3-Key Triple DES, HMAC, RSA, and ECDSA key types
- TLS and on-demand backups with SSH key authentication, for secure administrator remote access
Application Programming Interfaces (APIs)
- OASIS KMIP (Key Management Interoperability Protocol)
- RESTful interface API
- KMS
Custom Integrations
- Simplified RESTful API interface for key CRUD (Create, Read, Update, Delete) operations and crypto
- Supports open client libraries such as KMIP, OpenKMIP and PyKMIP
- Conforms with KMIP 1.0 through 2.1 specifi cations
- Implements auto-registration with native XML-based KMS protocol
- NIC Teaming Support
High Availability
- Highly redundant hardware to ensure highest operation continuity
- Active-active cluster with thousands of notes per cluster, supporting thousands of clients and millions of keys
- Automatic key replication and hands-off administration
- Audit logging
Pre-Installed Software
- Comprehensive monitoring, recovery, scheduled backups, log rotations, and restore functionality
- Web browser GUI and Command Line Interface supported
- SNMP alerts and SIEM log monitoring
- TLS and on-demand backups with SSH key authentication, for secure administrator remote access
Security and Compliance
- Meets NIST SP 800-131A Standards
- FIPS 140-2 Levels 1, 2, 3 and 4 (physical) (depending on the ESKM Deployment Option
- Compliant CC EAL2+
- Meet audit and compliance mandates with controls for PCI-DSS, HIPAA, EU data privacy laws, and other regional privacy mandates
Ease of Use
- Certificate-based mutual client-server authentication, secure administration, and audit logging
- Performs automatic key replication, client load balancing, and fail-over
- Embedded Local Certificate Authority as an optional feature
- Automated backups
- Client failover




















