The realization of Zero Trust
In this article, we summarize our earlier 6 part series on Zero Trust, highlighting key principles that have been written as a guidance to help organizations to design and review a zero trust network architecture, helping them to meet their individual requirements.
A Zero Trust approach should be applied across an organization's entire digital estate as an integrated security philosophy and end-to-end strategy.
Here you can read the articles in this Zero Trust series:
Introduction to Zero Trust Architecture
Identity Management in Zero Trust
Data Encryption and Access Management in ZeroTrust
Zero Trust with Right Key Lifecycle Management
The evolution of IT infrastructures, modern business models, digital transformation, and migration towards cloud-based applications resulted in the redefinition of security perimeters of organizations. Developments during the COVID-19 pandemic emphasized on “work from home” approach which also blurred the digital boundaries of organizations. All these technical enhancements resulted in an exponential increase in cyber threats and vulnerabilities.
It has been clear to cybersecurity professionals that the legacy and classical access control mechanisms (allowing inherited trust and absence of continuous validation) can’t defend organizations from modern-day attacks.
Zero Trust Model
As you can read in our introduction article, zero trust is a collection of policies, initiatives, principles, architectures, and frameworks based on the “Never Trust, Always Verify” model. Zero trust security undertakes that any device, user, or resource is not trusted and therefore must always be verified before access is granted and frequently evaluated for further sessions and activities. Fundamentally, zero trust is a model of extremely granular and distributed trust based on users, computing session scenarios, systems, and data.
Identity Management
The Zero Trust model's foundation is identity management since identities must be authenticated and authorized before any access to resources is granted. Users, applications, or IoT devices located on the Zero Trust control plane may make up identities. The use of diverse technologies and techniques is necessary to achieve zero trust in identity management, but organizations must first analyze their needs to design a comprehensive strategy. Several of these tactics include the following:
- Multi-Factor Authentication (MFA): Zero Trust mandates MFA which requires multiple authentication factors. MFA has noticeably secured identity management security where users are required to identify themselves through more than one authentication factor such as Something you know e.g., username/password, something you have e.g., OTP code/Smart card, and Something you are biometric or retina identity.
- Contextual Identity Management: The Zero trust model requires continuous validation of identities and their contexts. Organizations can increase and modify context workflows as per their security requirements. The common context factors are network, location, user groups, and devices.
- Single Sign On (SSO): SSO resolves the issues of fragmented identities by enabling users to maintain a single set of credentials to access multiple applications and services. SSO augments in minimizing the number of credential-based attacks, resolving security gaps due to fragmented identities caused by using both on-premises and cloud solutions
Authentication
Authentication is the crucial next step in putting Zero Trust into practice. The setup and administration of the network are done by Zero Trust components using the control plane.
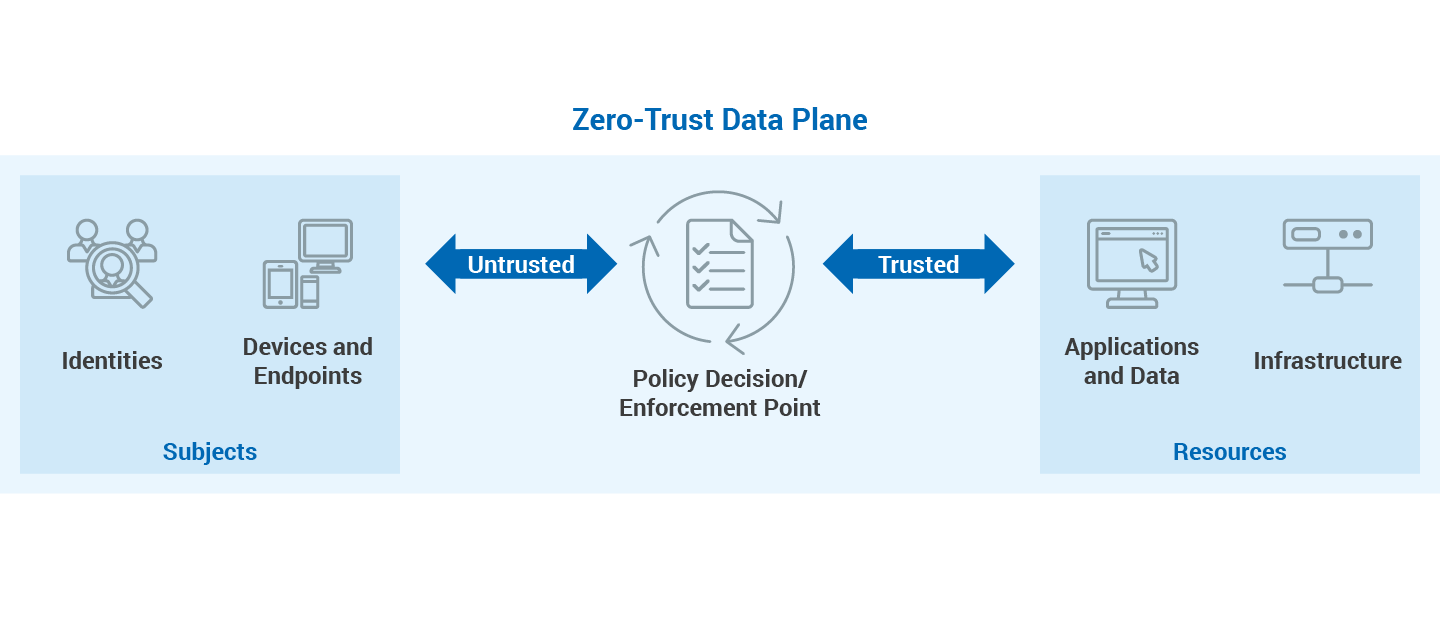
Strong authentication is used to verify an identity when it tries to access a resource, ensuring that the access is appropriate and normal for that identity. In Zero Trust, the following types of authentications are available:
- User or service authentication: The first aspect of authentication in Zero Trust is to authenticate the user, service, or application conclusively to make sure that the entity requesting access is the originally registered entity. Public Key Infrastructure (PKI) and Multi-Factor Authentication (MFA) are generally preferred.
- Device authentication: The second aspect of authentication in Zero Trust is to authenticate the device requesting access since it is as significant as the user or application itself. Another aspect may be the MFA with profiling and posturing of the client device.
Data Encryption
By preventing unauthorized access to sensitive organizational data, encryption has established itself as the foundation of contemporary cybersecurity. It is also essential for the deployment of zero trust architecture. End-to-end encryption (E2EE) refers to the idea of protecting data while it is in use, transit, or at rest.
- Zero Trust for Data at Rest: Most businesses have switched from traditional on-premises hardware solutions to cloud-based ones for their computing needs. It is strongly advised that businesses only use cloud providers and databases for data at rest that support and implement encryption mechanisms because they store, process, and transmit personally identifiable information (PII) and protected health information (PHI).
- Zero Trust for Data in Transit: Data in transit refers to data that is moving from one location to another. When data is in motion, it is generally less secure than inactive data given its exposure across the internet or private corporate network. As a result, data in transit is a potential target for hackers.
- Zero Trust for Data in Use: Confidential computing enhances Zero Trust by providing a secure execution environment for critical tasks and sensitive workloads in untrusted environments. Encrypted data must be decrypted for processing. However, a malicious application or compromised host may be able to access unencrypted, sensitive data. To safeguard currently-used data, it is necessary to use several techniques and technologies, such as the Trusted Execution Environment (TEE), Homomorphic Encryption (HE), and Confidential VMs.
Access Management and Control
In Zero Trust, every access attempt is by default untrusted, coming from an untrusted user, from an untrusted device, from an untrusted network, and must undergo extensive validation, according to the zero-trust access management architecture. The trust demonstration in compliance with the organizational security policies is a part of the verification procedure. The following factors must be taken into account for proper access control to be implemented effectively for organizations:
- Segmentation and Micro-Segmentation: The incorporation of network segmentation in the organizational infrastructure augments in splitting to further diverse zones or sub-networks which can limit the movement to other networks or zones once unauthorized access is gained.
- Extra Protection of Privileged Accounts: Zero Trust emphasizes that organizations should categorize and make an inventory regarding all the privileged accounts and their corresponding secrets, passwords, and credentials. Based on this intelligence, organizations can further implement access control mechanisms for the safeguarding of privileged accounts.
- Proxy-based Access Management: The integration of a control or proxy layer to assess the access policy for each application and application page is further highlighted by the implementation of access management in zero trust. The proxy layer protects the system's resources overall using centralized policies and contextual data to approve or deny access to particular resources.
- Adaptive Access Controls: These controls loop back contextual information, also known as "intelligence," into the security mechanism. Zero Trust implements adaptive access controls that manage access requests based on a context-based Just-in-time (JIT) approach to pause and dismiss sessions in response to user behavior, inappropriate activity, or changes in context and risk.
- Least Privilege Principle: The least privilege concept must be strictly enforced by organizations through enterprise-level policy across all networks and systems within the organization, together with attribute-based access controls. To restrict the permissions associated with particular processes and people, the least privilege principle also closely coordinates with the separation of duties and segregation of duties.
- Monitoring and Logging: The need for logging and monitoring tools to be in place for system security is further highlighted by zero trust. Monitoring the privileged access prevents harmful insiders and foreign attackers from succeeding in their attacks.
Cryptographic Key Management based on Hardware Security Modules
With the use of cryptographic keys, Zero Trust eliminates the antiquated idea of a "safe network" and employs data encryption and strong identity verification. Greater security and compliance requirements are both met by keys based on Hardware Security Modules (HSM). An HSM fulfills two main functions in regards to cryptographic keys:
- Secure Key Generation: Random number generation is the foundation for the development of cryptographic keys. HSMs use hardware-based TRNGs (True Random Number Generators), which produce real-time random numbers from physical sources of entropy as seeds for the secure creation of individual cryptographic keys.
- Protection of Cryptographic Keys: The secure storage of the cryptographic key is another crucial component that ensures it cannot be read, used, or exported in an unauthorized way. HSM-based key management and storage are assessed/tested as per international standards/compliance and offer greater security than software-based key stores (stored in programs and operating systems).
Every organization has unique challenges due to their current security strategy and levels of digital transformation maturity. Build your Zero Trust architecture with Utimaco.
Utimaco provides solutions that enable organizations to meet the components and principles of a Zero Trust architecture.