HSMs use key block structures as basic structures to achieve secure key management. This article introduces into the Atalla Key Block, explains its principle and details why protecting keys is so important.
The Backstory of Atalla Key Block
The Atalla Key Block is linked to the history of its inventor, Dr. Mohamed Atalla (1924-2009), an Egyptian-American inventor. Dr. Atalla is internationally known for inventing the MOSFET (metal-oxide-semiconductor field-effect transistor) in 1959. However, he also created the Atalla Corporation in 1973 to commercialize the “Atalla Box,” a Hardware Security Module and other devices to encrypt PIN and ATM messages. Dr. Atalla is often referred to as “the father of the PIN” because of the pioneering work he performed regarding PIN authentication.
One of the main functions of the Atalla Box is the use of key blocks. Key blocks are needed to securely interchange symmetric keys or PINs with other actors of the banking industry. This secure interchange is done with what is known as the Atalla Key Block format (AKB).
The Atalla Corporation was merged and acquired by several companies, including Micro Focus. Utimaco acquired Micro Focus in October 2018.
Principle of the AKB
In principle, HSMs use key block structures as basic structures to achieve secure key management. A key block (or key bundling) is a data structure used to store or exchange cryptographic keys within hostile environments.
As a minimal requirement:
- Key blocks should be encrypted;
- Hardware security modules should be able to determine the correct key usage via control information;
- Tampering should be detected via a dedicated secure mechanism.
The Atalla Key Block was the first implementation of a secure key block that met these requirements.
An Atalla Key Block securing a key consists of three parts:
- An 8-byte header containing the attributes of the key (header);
- A 48-byte key field containing the Triple-DES cipher block chaining (CBC) mode ciphertext of the key (encrypted key field);
- A 16-byte field containing the Triple-DES message authentication code (MAC) computed over the header and the encrypted key field.
Atalla Key Block was the origin of several standards. The Atalla key block format is; therefore, de facto integrated to the following standards:
- ANSI X9.24 Part 1-2009 Retail Financial Services Symmetric Key Management Part 1: Using Symmetric Techniques;
- ANSI X9.24 Part 2-2006 Retail Financial Services Symmetric Key Management Part 2: Using Asymmetric Techniques for Distribution of Symmetric Keys;
- ANSI X9 TR-31, Interoperable Secure Key Exchange Key Block Specification.
To better understand what the Atalla Key Block is, and before detailing its principle in detail, we must first understand the problems it had to solve originally.
Why Protecting 3DES Keys (and Others) Matters
DES has been used for a long time as an encryption mechanism in the banking industry, especially in ATMs. The banking industry massively moved to 3DES when DES-breaking machines using key exhaustion attacks were successfully built. The first known DES-breaking machine was built in 1999 by the Electronic Frontier Foundation (Deep Crack). Later on, a second machine was built by the COPACABANA (Cost-Optimized Parallel Code Breaker) project.
3DES uses either 2 keys of 56-bit length or 3 keys of 56-bit length. The problem is that incorrectly stored and protected 3DES keys do not guarantee any better protection than using 56-bit DES keys.
Because of limitations, keys cannot always be stored in the memory of an HSM. But regardless of that, cryptographic keys must be protected throughout the cryptographic life of the data or process being protected. In the case of PIN protection in a consumer banking environment, the lifespan of the data or process may last for many years.
In addition, keys must be shared among HSMs at a host site and transmitted to other systems. This is the problem of secure key exchange - the transmission of cryptographic keys between disparate systems.
There are many scenarios in which attacks can be done against 3DES in the context of the banking industry. As per the ANSI X9.24 standards, 3DES key should be ciphered using 3DES encryption. Each of the 2 encryption keys K1 and K2 [1] of length 56 bits each should be ciphered by 3DES, which keys will be stored in a database.
Let us suppose that an attacker, which could be a disgruntled employee or a rogue contractor or vendor, wants to target the 3DES keys stored per the ANSI X9.24 standards.
The 3DES key is (K1, K2).
K1 is ciphered by 3DES with keys (C1, C2) and K2 is also ciphered by 3DE with keys (C3, C4).
We suppose that the attacker can have the security module ciphering a text T with the key C1 as a single-DES operation, resulting in a ciphered text T’.
That attacker can break the cipher T’ and uncover the key C1 using, for example, a COPACABANA machine, as previously described. That technique could be repeated with C2, C3, and C4 to uncover the 3DES key (K1, K2). This is not exactly unrealistic because, in the banking industry, many HSMs must maintain single DES operations for legacy reasons.
Because of the control information header and the overall MAC, an attacker could not use that technique against 3DES keys protected by an Atalla block format. And this is exactly why the Atalla block format was invented.
Detailing the Principle of the Atalla Key Block Format
Here we detail how the Atalla Key Block is being processed by a receiver to extract the key (or PIN) it protects.
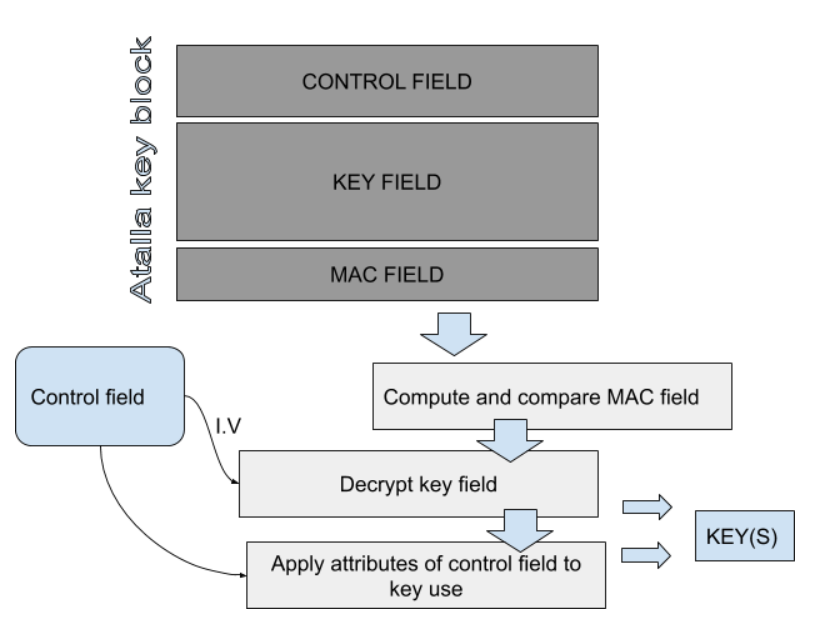
First, the AKB is checked for integrity by computing the MAC and comparing it to the presented MAC field. If the MACs are the same, the operation continues. The key is then decrypted using the Control Field Initialization Vector I.V) and a first variant of the master file key. Keys are then resolved and used following the data from the control field. The control field is an 8-byte header which details all the information about the key within the block.
|
Byte |
Description |
|
0 |
Version number for the format |
|
1 |
Key usage |
|
2 |
Algorithm |
|
3 |
Mode of use |
|
4 |
Exportability |
|
5 |
Padding flag |
|
6 |
Special handling information |
|
7 |
Other information |
As you can see, a lot of information is presented in the header which makes AKB very flexible for different use cases.
The key usage can be one of the following options:
- ATM Master Key
- CVV
- Data encryption
- IV
- Key encryption
- MAC
- Manufacturer defined
- PIN encryption
- Reference PIN Block
- Signature
- Token key
- PIN Verification
- Translation and conversion table
- Communication Key
- Derivation Key
- Master Key
- Diebold Number
The Key Block can handle the key for the following algorithms:
- Manufacturer defined
- SHA-1
- RC2/MD2
- IBM 3624
- RC4/MD4
- RC5/MD5
- IBM4731
- ANSI
- Atalla
- DES/3DES
- EMV KEY DERIVATION
- Diffie-Helmann
- AES
- SSL
- RSA
- DSA
- VISA
- ECC
While the most frequent use in banking is 3DES, AES or RSA can also be secured by the key block.
The “Mode of Use” flag is usually: Encrypt, Decrypt, Generate, Verify or no restriction at all.
Other useful information will be conveyed in the next bytes of the control field.
Conclusion
The Atalla Key Block is a very important format, and is at the root of all cryptographic block formats found within PCI and ANSI standards. It solves important issues regarding the security of keys when they are in transit within a potentially hostile environment.
Read more about the Utimaco Atalla AT1000 Hardware Security Module (HSM), a payments security module for protecting sensitive data and associated keys. Or access more blog articles on the Utimaco Atalla AT1000.
References and Further Reading
[1] 3DES is usually used with 2 different keys. Using 3DES with 3 different keys doesn’t bring more security than with 2 keys because it is vulnerable to a Meet-In-The-Middle attack.
Blog post by Dr. Ulrich Scholten