Enable the encryption strategy for your business in an instant
Protecting sensitive data has never been easier: u.trust LAN Crypt Cloud helps you implement complete file and folder encryption in your organization. First define the assets and locations to be protected - then use access management to allocate permissions. The role-based user management makes it easy to onboard new employees, so you don't have to create a whole new profile for each user. Benefit from:
- Easy setup in less than 15 minutes
- Role-based encryption of sensitive and business-critical data
- Protection against unauthorized internal and external data access
- Fulfillment of individual security policies and compliance rules
- Cross-platform and transparent data access
Product Type:
As-a-serviceAvailability:
Key Benefits
Compliance for GDPR and cross-platform data protection
Achieve compliance for GDPR and similar data protection regulations
Whether GDPR, ISO 27001, NIS2, or HIPAA: Integrating u.trust LAN Crypt into corporate processes makes certification and compliance easier for you. Manage your data protection policies from a single dashboard that gives you visibility into devices, users, and other information – a powerful tool for simpli-fying compliance audits.
Cross-platform data protection
Client-side encryption protects your data everywhere: on cloud platforms like OneDrive, Google Drive, and others, as well as on local servers, hard drives, mobile devices, and removable media. Experience peace of mind knowing that encryption occurs seamlessly in the background for employees, eliminating the need for complex workflows.
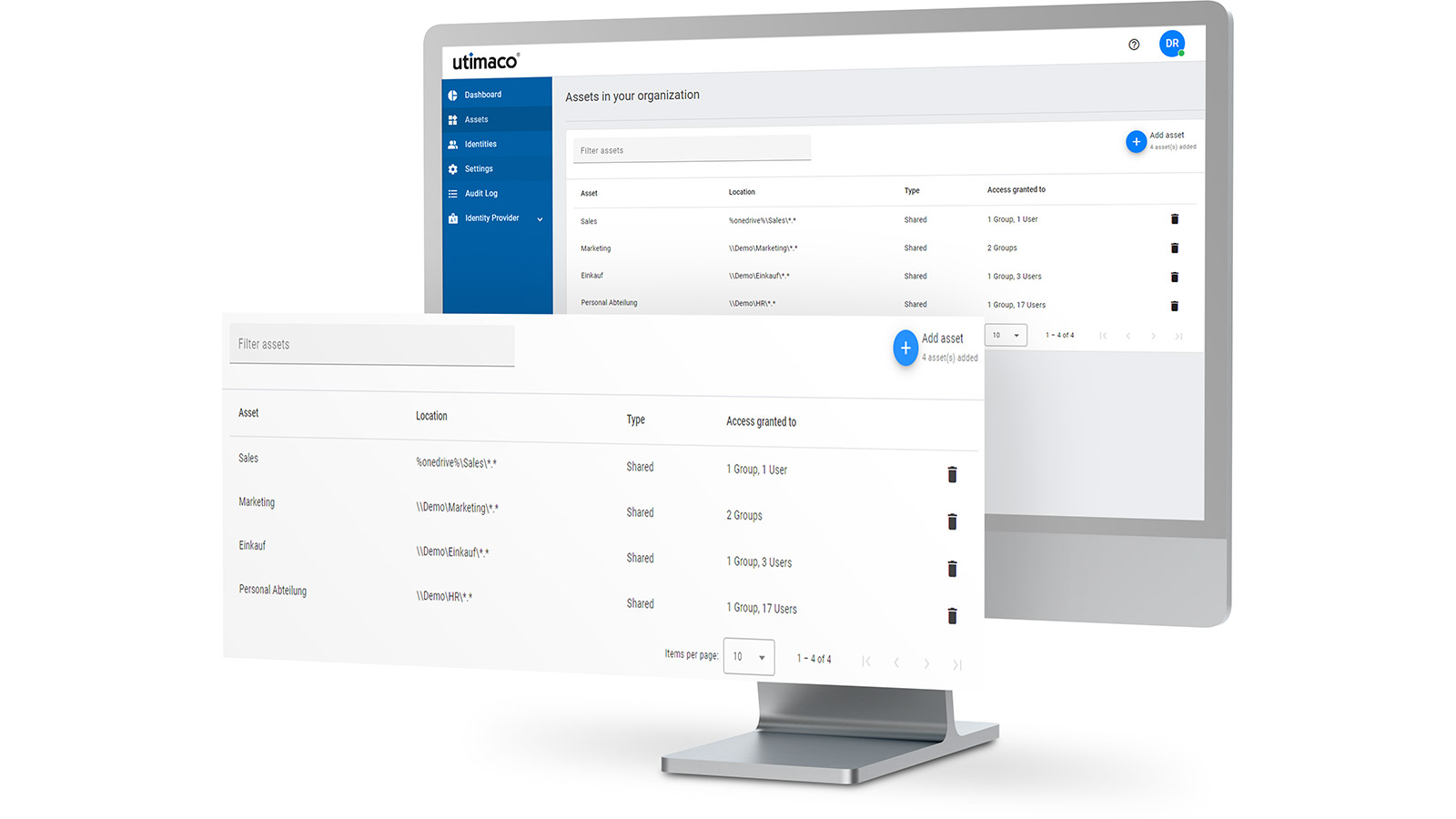
Easy administration of access rights and encryption rules

The easy administration concept allows you to set up your environment in just three steps:
- 1. Define assets to be protected
- 2. Define identities for your users
- 3. Distribute access permissions
Try File and Folder Encryption as a Service free for 30 days
Sign in with Microsoft
For a centralized and seamless sign-in, File and Folder Encryption as a Service offers users the possibility to connect their accounts to their organization's Microsoft account. The 'Sign in with Microsoft feature' provides a simple, secure way to sign into LAN Crypt File and Folder Encryption using a Microsoft account. Administrators can define which account users must use to log in to the LAN Crypt service - their LAN Crypt account or their Microsoft account.
File and Folder Encryption as a Service - Flexible licensing to fit your use case
| Discover | Standard | Advanced | |
|---|---|---|---|
| LAN Crypt File and Folder Encryption App for Desktop and Mobile: Windows, macOS, Linux, Android, iOS | ✓ | ✓ | ✓ |
| Central key management in the cloud admin | ✓ | ✓ | |
| MS Entra ID / Azure Active Directory integration | ✓ | ✓ | |
| Device synchronization for password generated keys | ✓ | ✓ | |
| Cloud backup for password generated keys | ✓ | ✓ | |
| 0,99€ (per user / month) | 7,99€ (per user / month) | 10,99€ (per user / month) |
Technical Specifications
Technical Requirements
Client 64 Bit
- Windows 10 Pro/Enterprise
1809 (LTSC)
20H2
21H2
21H2 (LTSC)
22H2 - Windows 11 Pro/Enterprise
21H2 and 22H2 - Windows Server
2019
2022 - Supported Citrix Environments
Citrix Virtual Apps and Desktop 7 1912 LTSR CU2 on WS 2019 - macOS
10.15 Catalina
11 Big Sur (M1 & Intel)
12 Monterey
13 Ventura
Administration 64 Bit
- Windows 10 Pro/Enterprise*
- Windows 11 Pro/Enterprise*
- Windows Server*
Mobile Operating Systems
- Android 10, 11, 12, 13
- iOS / iPadOS 15, 16
Supported Media and Platforms
- Media
Network drives
Local hard disks
CD / DVD
USB
Flash drives
Memory cards - Platforms
Microsoft Terminal Server
Virtual Machines
OneDrive
Azure SQL
Dropbox
Google Drive
MS Azure (e.g., Clients, Azure, DB)
Supported Databases
- Microsoft SQL Server
2019
2022 - Oracle Database
19
Supported Algorithms
- Encryption
AES 128 Bit and 256 Bit
3DES 168 Bit
DES
IDEA 28 Bit
XOR - Certificates
RSA up to 4096 Bit
Self-generated or via PKI
Soft certificates
Smartcards
Tokens - Recommended algorithm
AES-256 - Recommended encryption format
XTS-AES - Hash
MD5
SHA256
* See client versions for supported versions





