Connectivity has the power to transform. However, it doesn’t come without risks. The vast collection of highly sensitive data in connected vehicles necessitates an entirely new level of security, particularly against ransomware, cyber war, and other cyberattacks that exploit software and hardware flaws. Given the increasing complexity of the connected vehicle, It is critical to protect smart components and devices from the time they are manufactured until the end of their lifecycle.
Who’s ‘driving’ your vehicle?
When we refer to 'connected vehicles,' we are referring to vehicles that have interconnected systems that send wireless data about the driver and internal systems back to the manufacturer. Comprised of multiple amounts of hardware and software components across a complex supply chain, in many respects, a connected vehicle can be considered to be a ‘computer on wheels’.
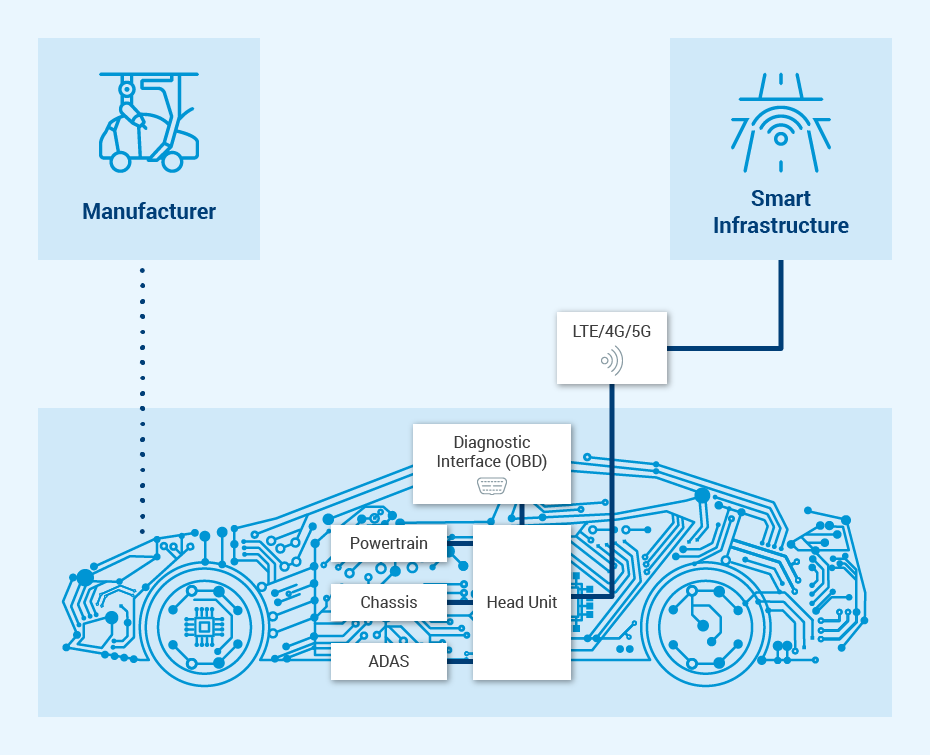
Due to the integration of numerous automated driving features and a wide range of communication interfaces, connected vehicles have a complex architectural design. In addition to endangering the safety of other road users, a successful external attack on such features has the potential to seriously harm passengers' privacy and operations as well as organizations. As a result, the risk of cyberattacks escalates with increased vehicle connectivity.
Attackers can hack connected vehicles in a variety of ways. They can take advantage of flaws in the mobile app that controls the vehicle. They have the ability to disrupt the communication channel. They have the potential to hack into internal vehicle systems. They have the capability to attack the vehicle's backends.
If left unprotected, the entire vehicle supply chain is at risk to cybersecurity attacks
Connected vehicle threats
One of the most pressing issues confronting the automotive industry is cybersecurity. For this purpose, we look at it from 4 perspectives:
- Electrical components that act as small computers in charge of vehicle functions
- Communication between these components which represent the vehicle's entire system
- The multiple interfaces between the vehicle and externally
- Data transfer outside of the vehicle which could include data transferred to the cloud
Every smart component and device in the vehicle promotes connectivity which also means that every driver ‘convenience’ increases risk. To ensure the safety of the vehicle, smart components and devices must be protected from the point of manufacture until the end of the lifecycle. This is possible through device attestation, which enables all parts and information authentication at each access point and with each information exchange. Authentication aids in the protection of components and devices from tampering and ensures that they communicate securely and reliably.
Rather than patching extremely dangerous security flaws as they arise, vehicle manufacturers should address cybersecurity from the start.
Security by design – device attestation & key injection
All parts and information must be authenticated at each access point and with each information exchange. Are these parts and devices trusted? Or could they endanger the network? Attestation allows vehicle manufacturers to identify devices that have been tampered with.
Device attestation is used to verify the authenticity of the hardware - proof of origin at the manufacturing level. Each device must communicate securely and reliably with its manufacturer, the infrastructure, as well as other vehicles, including authorized third parties. To validate that the device is authentic and untampered, the manufacturer or service provider must take measures to ensure the authenticity of the firmware and software installed in automobiles and guarantee a tamper-free installation process.
Key injection enables manufacturers to provide reliable device attestation. The cryptographic keys are generated within the secure boundaries of a Hardware Security Module (HSM) and injected into the smart component such as Electronic Control Units (ECUs), that controls the mechanics of electronic features within the vehicle. This trusted injection process establishes the unique identity for each ECU ensuring its integrity throughout the production and operational life cycles to guarantee authenticity and tamper-free parts.
End-to-end security must be used by the manufacturer to protect all data and information exchanges in order to prevent data breaches and cyberattacks. Reliable end-to-end security is paramount.
Automotive cybersecurity
The increasingly interconnected nature of a vehicle’s control modules means there is no safety without security. Security features must include not just physical access and protection of confidential information, but also critical safety systems. To secure unauthorized access to embedded systems and data, automotive vehicle manufacturers must consider every type of attack.
Manufacturers typically have to choose between the cost of defending against an attack (or the revenue lost as a result of an attack) and the cost of mounting the attack because of the wide variety of attack mechanisms that are available (often referred to as the attack surface).
Embedded security measures provide a means of ensuring that security is not compromised, as well as safeguarding manufacturers' investment and drivers' privacy.
UTIMACO has accumulated a wealth of experience in securing data and devices for more than two decades and has created a distinct offering by recognizing the importance of device attestation and data security in the automotive sector.
Find out more about device attestation in our automotive white paper.