As we have seen in the introductory part about QR codes, QR codes in payment are not currently using any sort of encryption. While they can be a very convenient method of payment, they must be improved and made more secure. First, let us see what problems can occur when encryption is not used with QR codes in a merchant-presented or customer-presented context.
Problems linked to the absence of encryption with QR codes
QR codes have not been designed with encryption or any specific security features, except maybe Salomon-Reed error correction codes but this can hardly be considered as proving any sort of real anti-tampering. At the same time, since any sort of short information can be contained inside a QR code, it is very possible to use them to transport encrypted data.
Let see the problems created by non-encrypted data contained in QR codes in transactions such as described by EMVco.
Modified QR codes in Merchant-presented context
Since the consumer cannot really decode a QR code in itself (try it yourself…), there is no way to visually check that the payment data contained in the QR code are correct and represent exactly what is due by the consumer. Most of the time, QR codes are used so that the payment can be done fastly, with almost no interaction, except a quick scan. QR codes are often presented at the end of a bill printed on some ordinary paper. It doesn’t seem very hard for an attacker to substitute the original bill with a modified bill having different payment information: for example, a different amount to pay and/or a different bank account to credit.
Let us do a small experiment. We will generate first a merchant-presented QR code using a .NET library:
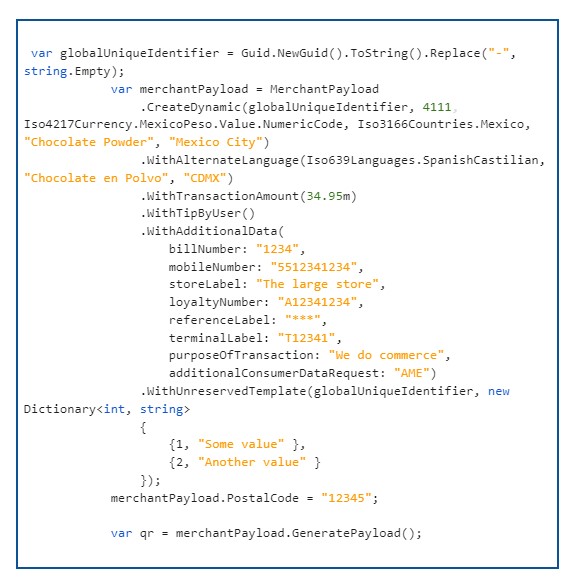
The EMV QR code raw value will be:
00020101021226360032f9989a044006476698ac2708be6fbef6520441115802MX5916Chocolate Powder6011Mexico City61051234564360002es0118Chocolate en Polvo0204CDMX540534.955303484550201629601041234021055123412340315The large store0409A123412340503***0706T123410814We do commerce0903AME80670032f9989a044006476698ac2708be6fbef60110Some value0213Another value6304E1CB
If we encode it in base64 and generate a QR code for payments, we will get this:

The consumer will scan this code and pay 34.95 Mexican pesos (1,50 EUR) to the merchant “The large store”. Of course the consumer is expecting to pay that amount of money but in the context of QR codes it is probable that this consumer will not be entirely focused toward carefully checking the information.
Now let’s imagine that this is the following code which is presented to the customer on a paper bill:

That is a valid EMV QR code, it contains the exact same payment information mentioned before… except that the transaction amount is now 3,495 Mexican pesos (150 EUR) and is to be paid to a different bank account.
One cannot expect the mobile device applications which will process these QR codes to be 100% perfect and so 3,495 may be displayed as 3495. There are great chances that a customer in a hurry will not double check and pay…
By looking at the QR code itself, the consumer has no way to tell the difference. While they are not encrypted QR codes are obviously hardly human-readable…
There are many other ways to tamper such a code and to fool a customer.
Fraud involving QR codes in Consumer-presented context
In the opposite direction, it’s the same problem: a consumer can easily display modified QR codes containing stolen credit card information and use them to pay fraudulently for goods and services.
Even if the consumer is honest, a rogue employee of the merchant could easily capture the QR code with a camera from a mobile phone and decode card information.
How HSMS can solve the situation?
QR code payment originates from Asia. They are convenient in a country where there can be a huge amount of people waiting to pay for goods and services at a cashier’s desk. However as we saw previously, there is absolutely no sort of security behind that payment system.
However the solution to the problem is simple: encrypting the QR codes themselves.
HSMs can provide cryptographic systems in order to generate and decipher encrypted QR codes in such a way that the QR code, which is an image, transits securely between the merchant and the consumer.
Why HSMs must be the root of trust for encrypted QR codes
In order to encrypt QR codes, sensitive keys must be used, they cannot be really used on the merchant device or on the consumer device as both are largely unprotected, they are often standard mobile devices. Therefore it is needed to contact an online service which will encrypt and decrypt on-demand the QR codes. Such services must use HSMs as a root of trust because only HSMs have the sufficient security to guarantee that the encryption and decryption will be done in a totally safe environment.
Safeguard yourself : use HSM for QR codes
Play safe! QR codes are a brand new method within the payment industry. They originate from Asia, and especially China. They are so new that EMVco had to issue an ‘emergency’ specification for them and truly they took everybody by surprise. Yes QR codes are convenient and solve many problems when a cashier has to process payments very fast. However as we underlined in this article, they are insecure. Play safe by using Payment HSMs which are certified for banking applications.
Blog post by Martin Rupp, a cryptographer, mathematician and cyber-scientist. He has been developing and implementing cybersecurity solutions for banks and security relevant organizations for 20 years. Martin currently researches the application of Machine Learning and Blockchain in Cybersecurity.